Enterprise Cyber Risk Resiliency
Cybersecurity Risk Management
ProcessUnity enables the CISO to prove cyber readiness with a single platform to monitor cyber risks, improve mitigating controls and prioritize program activities. Powered by automation, the platform is purpose-built to create a defensible cybersecurity risk management program that bolsters the organization’s resilience.
Powerful Cybersecurity Risk Management Tools
-
Baseline cyber program maturity and track progress towards targets
-
Monitor the severity, likelihood and impact of enterprise risks
-
Prioritize security improvements for risks, controls and policies
-
Align audit and certification efforts across one or multiple frameworks
-
Make smarter cybersecurity investments with real-time budget data
-
Deliver board-level summaries of cybersecurity program effectiveness
Gain Visibility with Real-Time Cyber Risk Monitoring
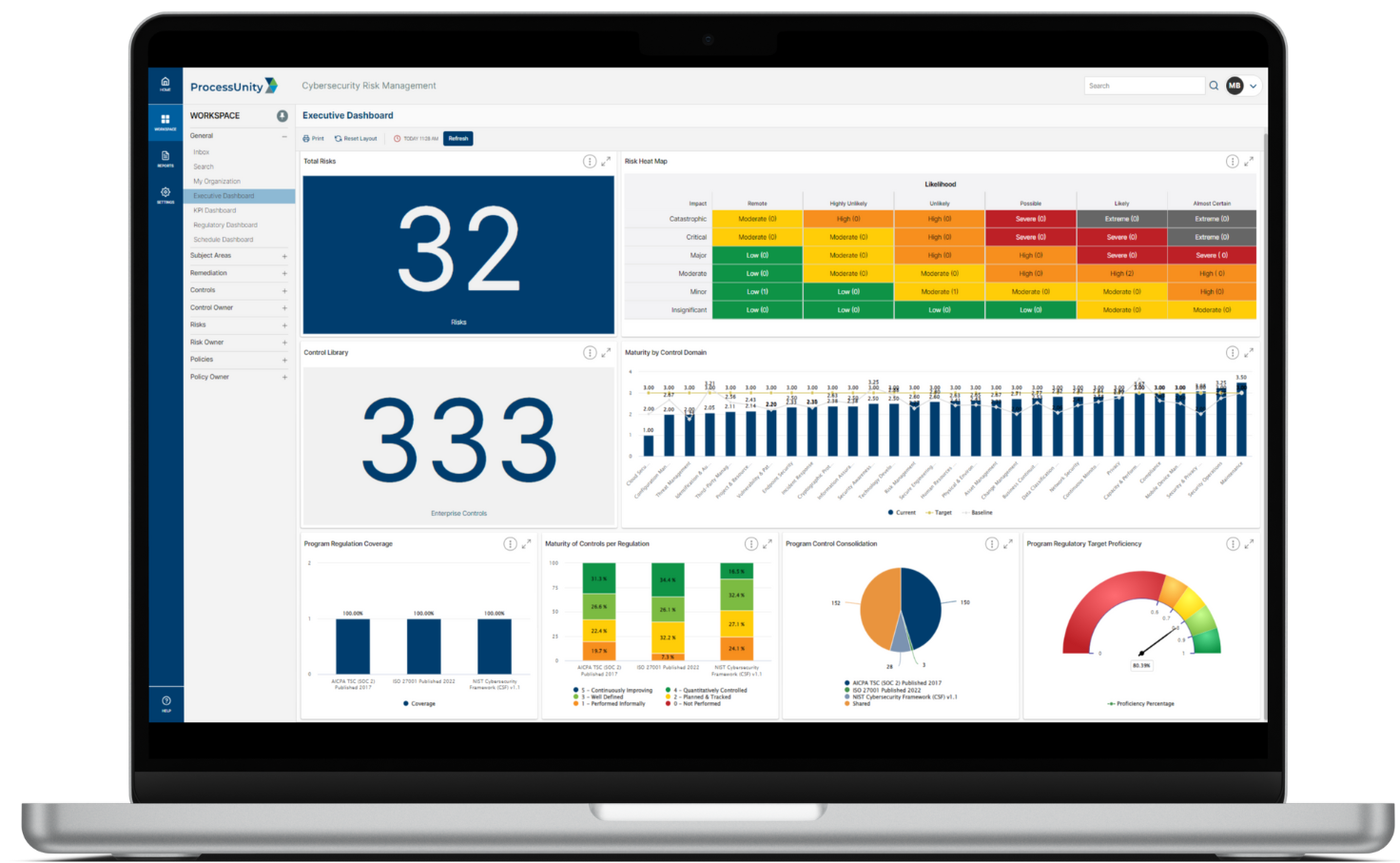
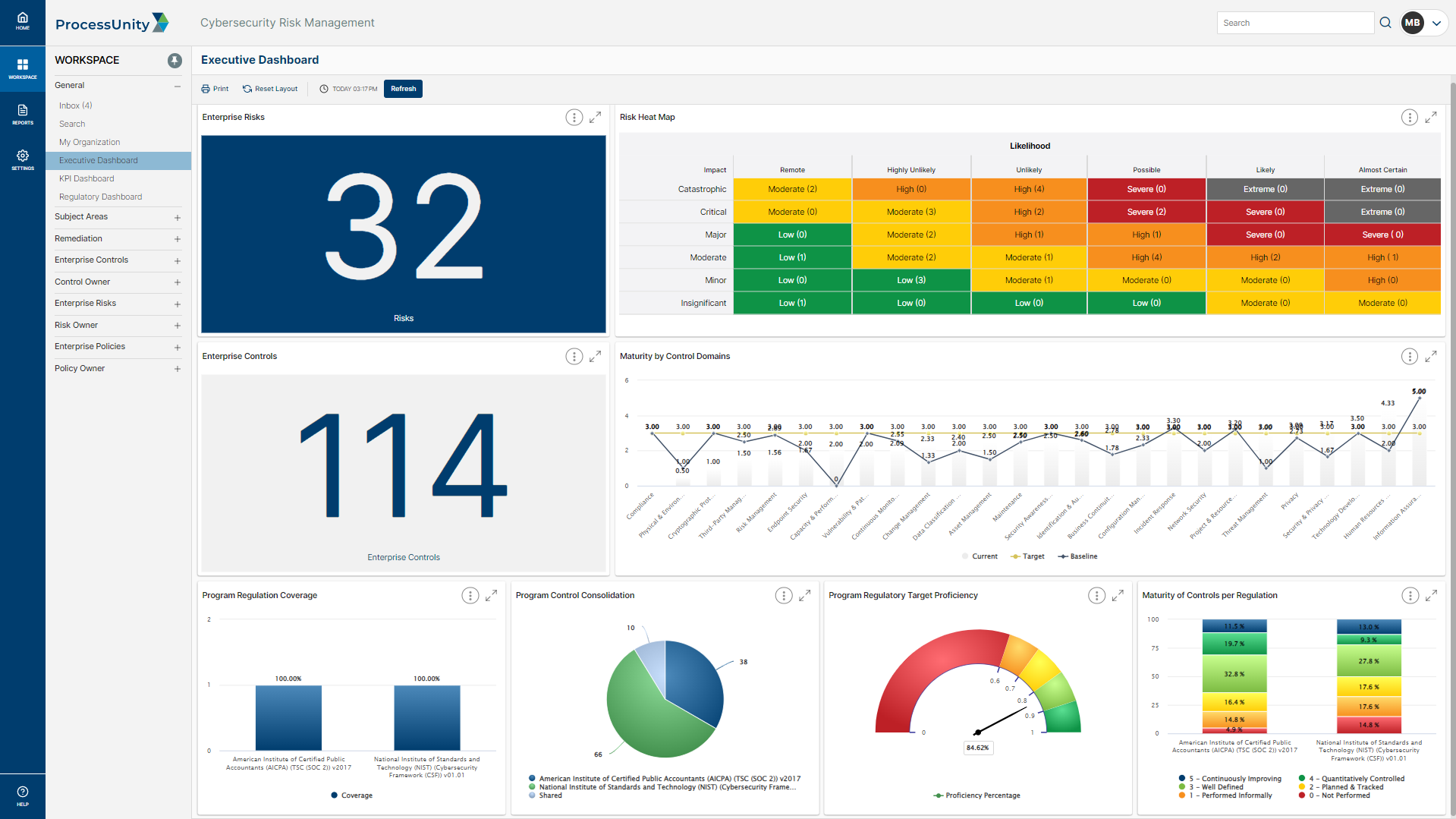
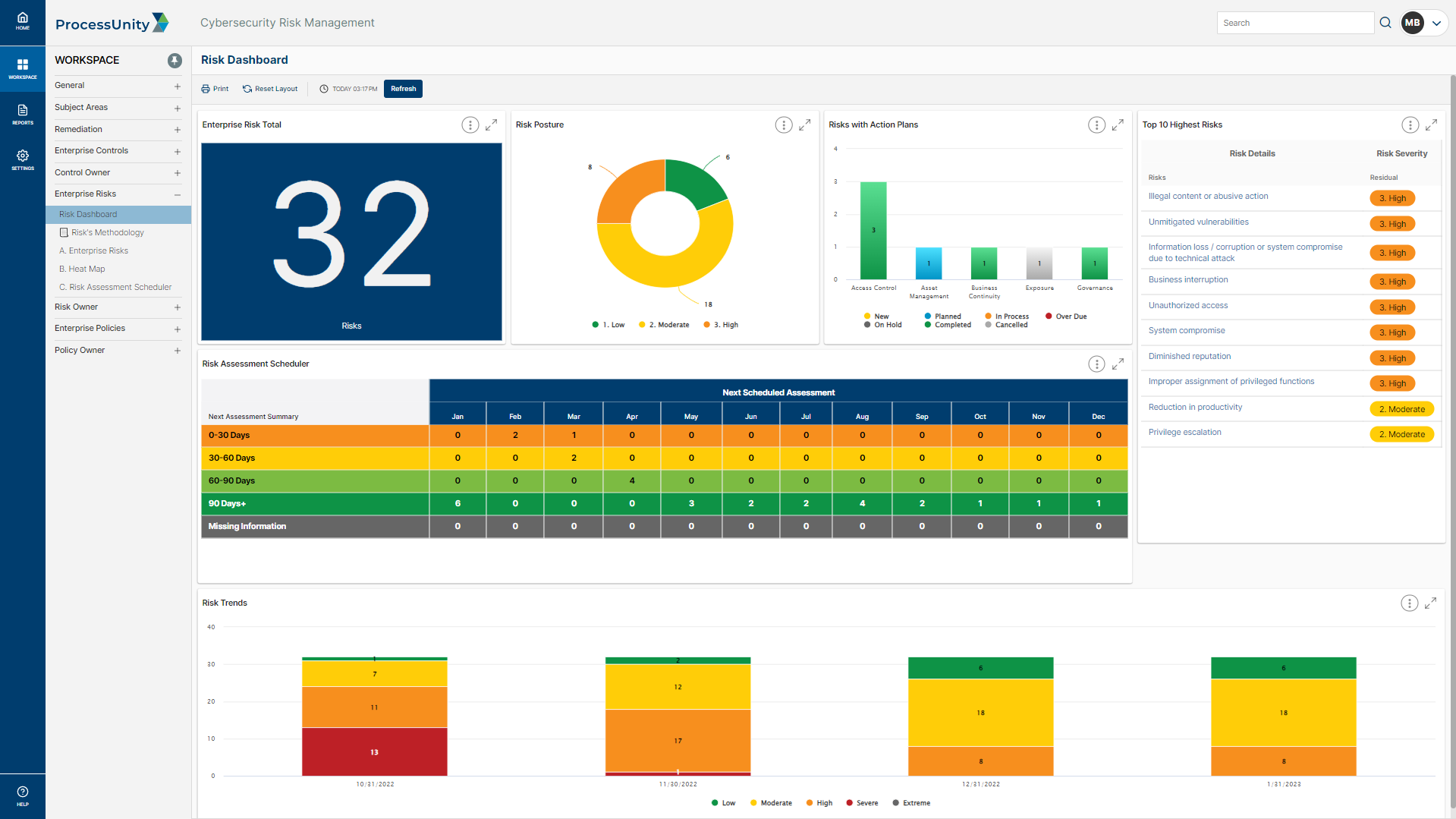
Effective security leadership starts with a complete view of your cyber risk landscape. With the ProcessUnity enterprise risk register you gain complete visibility into your cyber risks in a color-coded heatmap organized by criticality, allowing you to proactively monitor risks, lower their severity through targeted action plans, and deliver risk summaries to the right stakeholders.
The ProcessUnity enterprise risk register automatically calculates risk ratings based on severity, likelihood and impact, then maps risks to their mitigating controls and policies. Risk assessments are distributed on your schedule, automatically gathering evidence to inform risk analysis. Action plans can be created directly from a risk assessment to drive immediate improvements where needed.
Build a Robust Library of Cybersecurity Controls
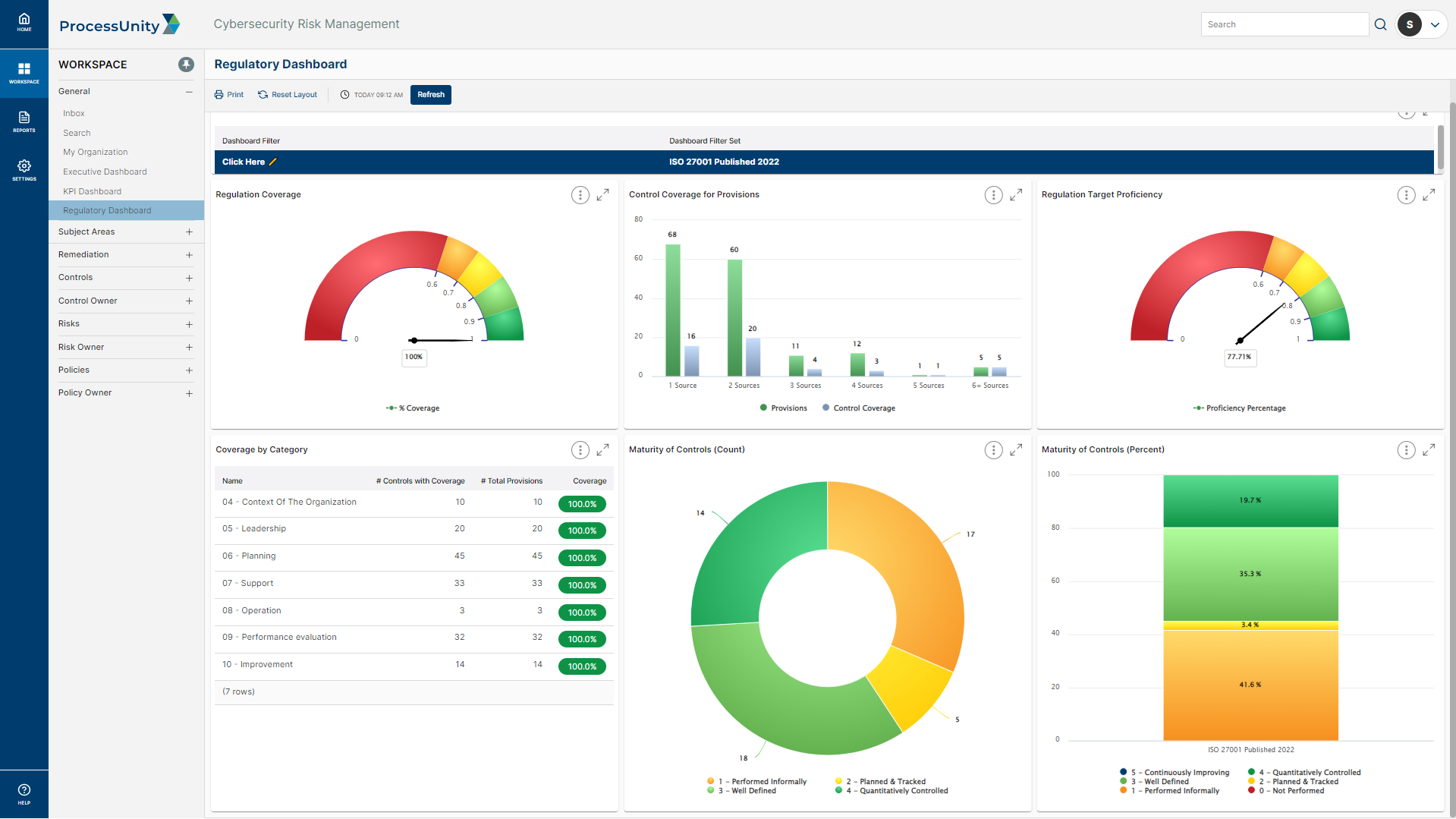
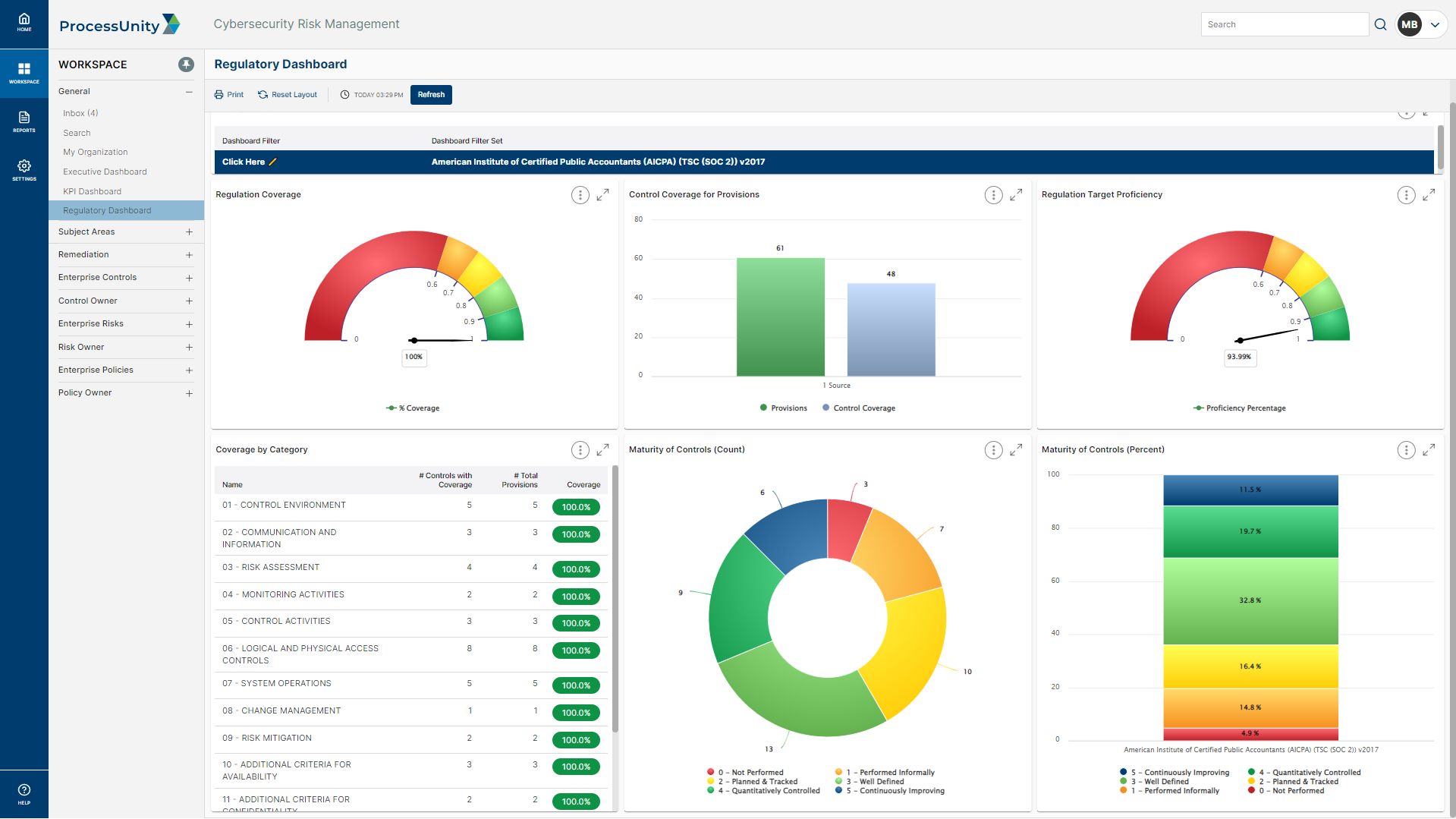
As the center of your cybersecurity strategy, your controls should seamlessly map to your organization’s relevant frameworks, regulations, standards, and internal policies. ProcessUnity combines a pre-mapped control framework with your program data, leveraging the overlap between controls and internal policies to eliminate redundancies. With an organized control library, you can focus on identifying gaps and improving weak controls to ultimately mitigate enterprise risks and maintain cyber compliance.
ProcessUnity builds your unique control library using a framework mapped to 1,000+ control standards, including NIST Cybersecurity Framework (CSF), NIST 800-53 and ISO 27001. Automated control assessments and evidentiary requests keep your control reviews on schedule, giving you the information needed to accurately measure control effectiveness (how well the control performs) and maturity (how well the control is designed).
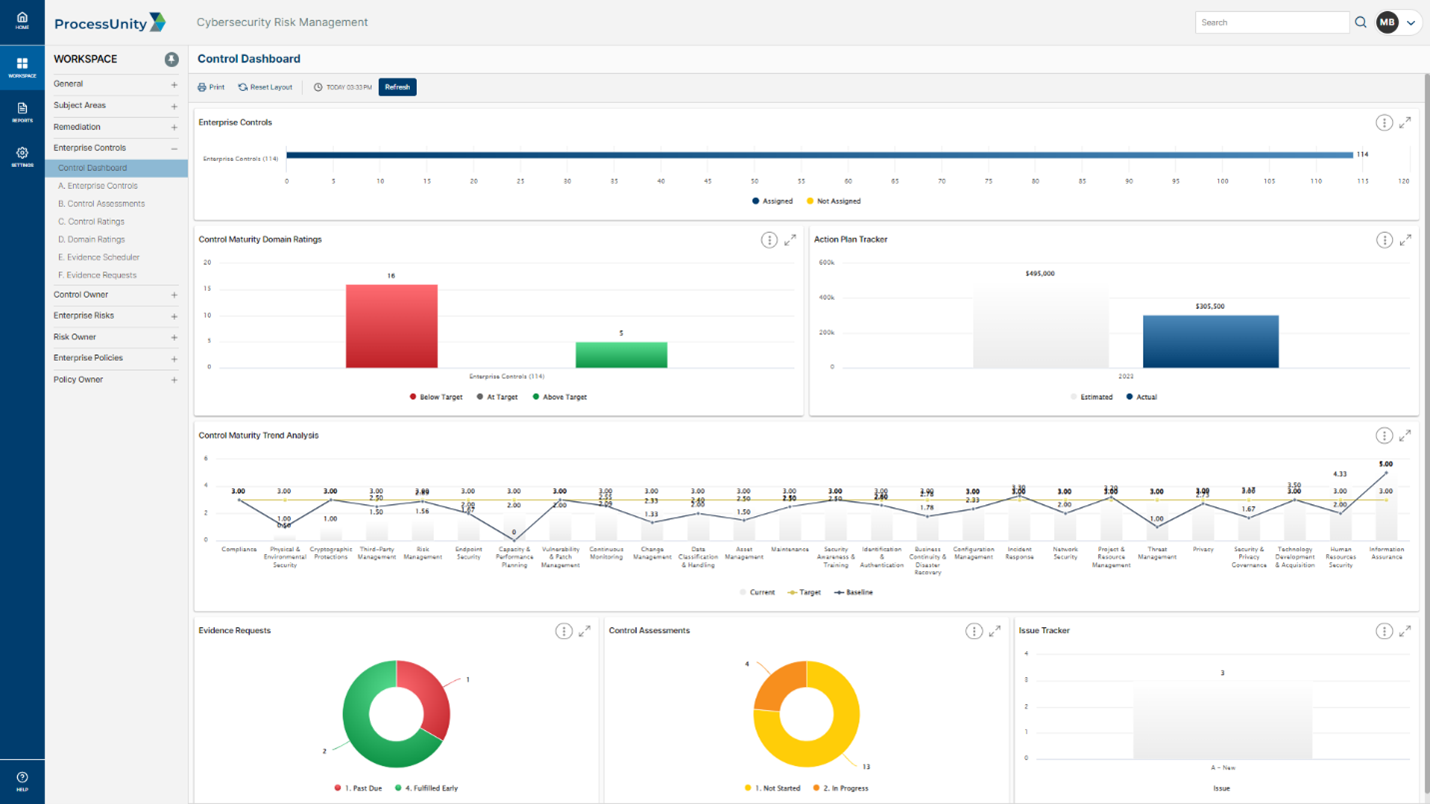
Optimize Your Mitigating Controls
Don’t wait for a security incident to find control weaknesses. ProcessUnity reveals control and domain-level gaps across your requirements, pinpointing the updates needed to bolster your organization’s resilience.
ProcessUnity automates control assessments with notifications and escalation reminders, ensuring that control testing remains on schedule. Once testing is complete, the platform creates an aggregated view of control effectiveness mapped to risks, then presents control analysis to guide project planning. Forecasts can be applied to open action plans, allowing you to understand the outcome of the planned improvement.
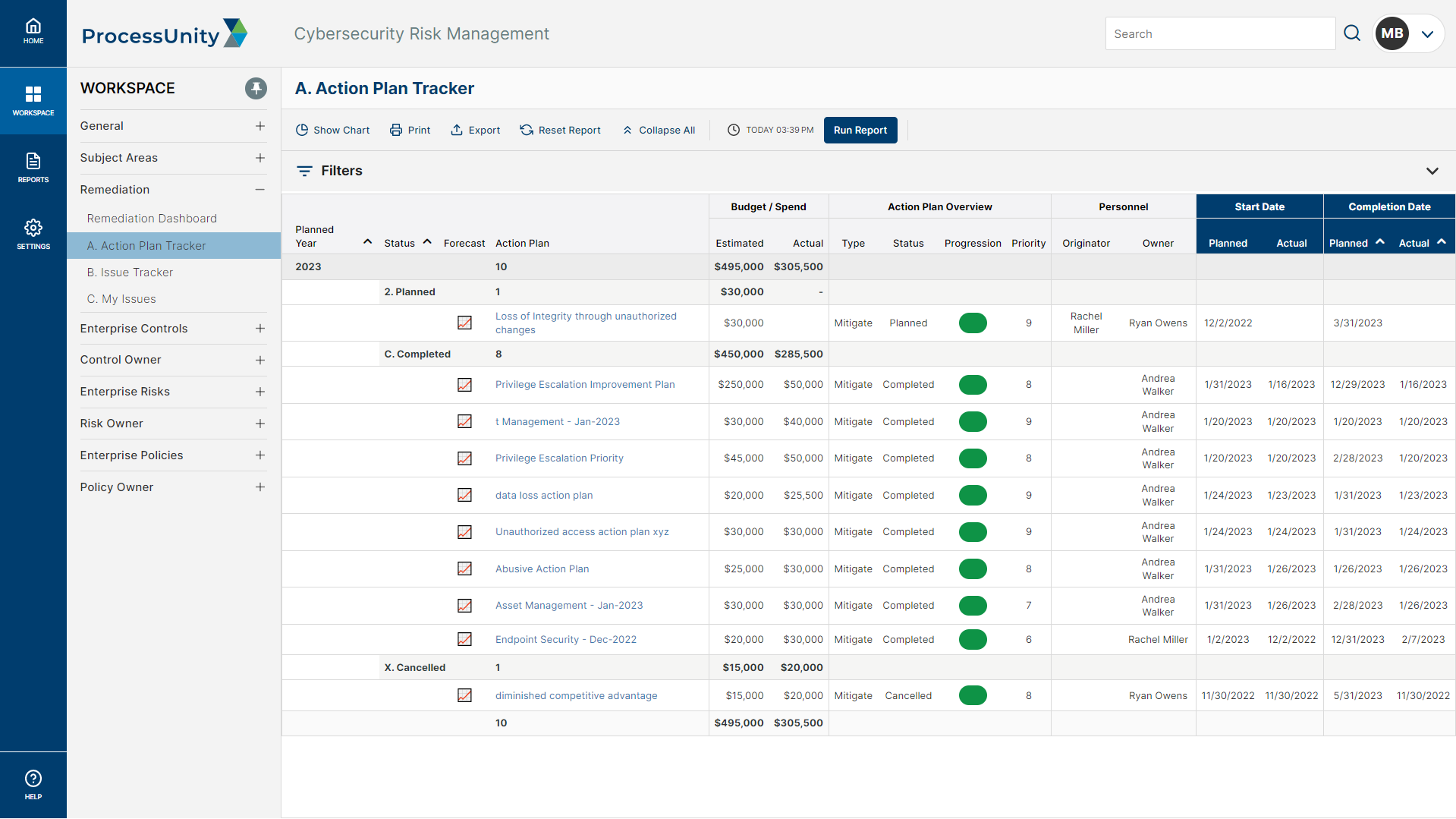
Make Smarter Cybersecurity Investments
Doing more with less is hard to achieve when all program activities feel critical. ProcessUnity optimizes budget spend by revealing where your investments are most effective across risks, controls, policies and action plans. By allocating spend to where it’s proven to mature your cybersecurity program, you ensure that cyber investments help mitigate risk and advance security posture.
The platform tracks budget spend against your program data – action plans, controls and risks – providing visibility into your program’s priorities. With a detailed report of your current and future budgetary requirements, you can make precise plans for your security roadmap and justify future requests.
Deliver Cyber Program Insights with Real-Time Reporting
When your organization’s leaders need proof of cyber readiness, they look to you for quick, data-driven reports. The Cybersecurity Performance Command Center gives you powerful tools and targeted intelligence to measure and communicate cybersecurity effectiveness. With the click of a button, you gain one-stop visibility into your program performance across risks, controls, policies, action plans and regulatory requirements.
Interactive dashboards provide you with real-time, drill-down insight into the state of enterprise-wide cybersecurity. In seconds, you can generate a custom, board-level report to demonstrate program performance to senior leadership and auditors.
Pre-configured, out-of-the-box dashboards include:
- Executive Overviews
- KPI Tracking
- Regulatory Proficiency
- Remediation Status
- Controls Effectiveness
- Controls Maturity
- Risk Prioritized Projects
Map to Common Frameworks, Regulations and Standards
Request a Demo: Cybersecurity Risk Management
Hundreds of organizations worldwide rely on ProcessUnity Cybersecurity Risk Management to implement a centralized system of record for managing cybersecurity activities across the organization. Contact us to start your journey today!
Request a Demo: Cybersecurity Risk Management