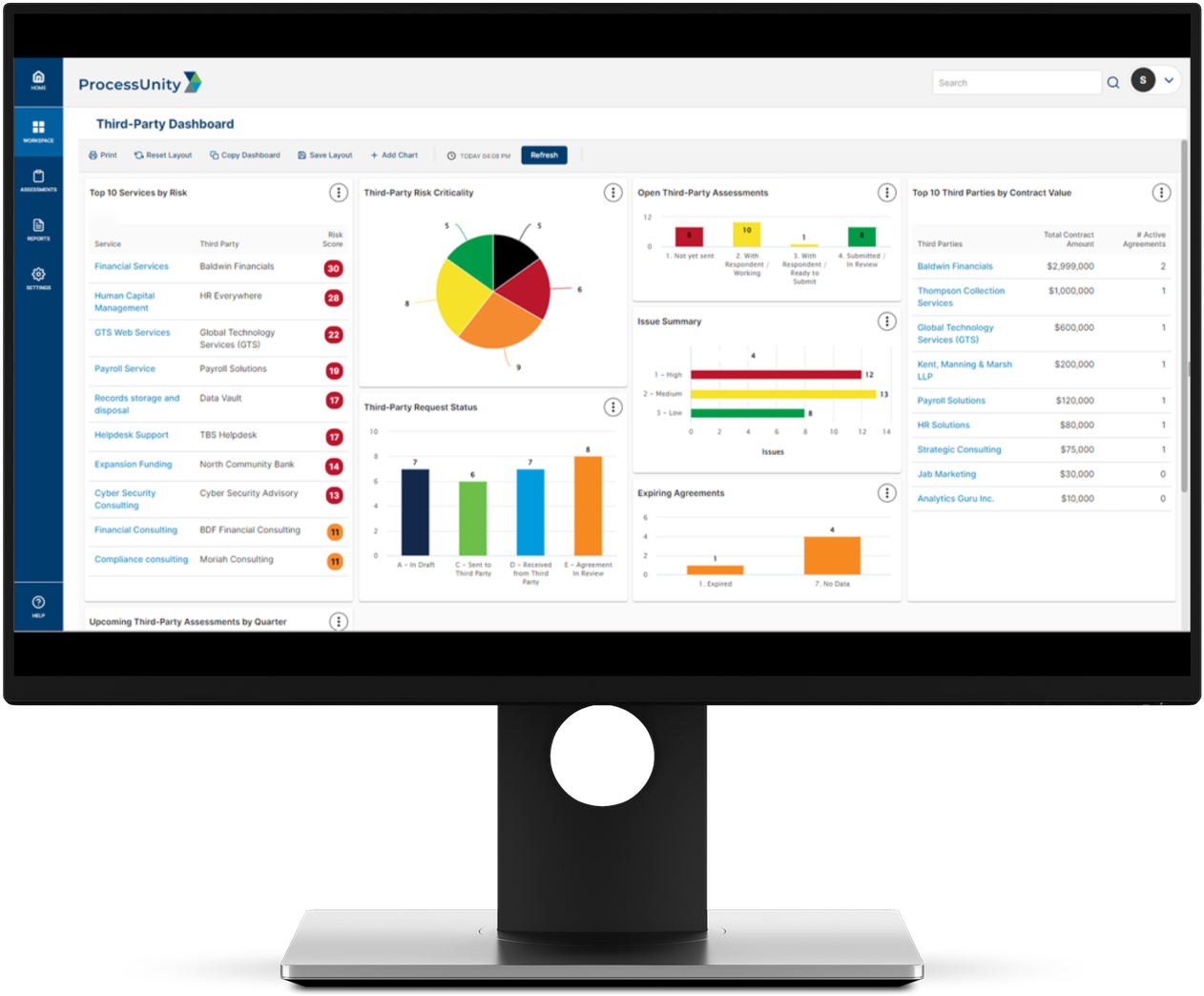
Risk Management Software
Scalable Software Solutions to Unify Risk Management
When teams work together, they maximize risk reduction.
To protect against the full spectrum of risk facing your company, you need to unify all risk management efforts inside and outside of the enterprise. ProcessUnity’s suite of future-proof software solutions helps align your risk reduction efforts powering an effective and efficient process for:
- Identifying
- Assessing
- Monitoring
- Remediating risk
The fully configurable, no-code ProcessUnity Platform and its seamless integration with corporate systems fuels risk unification across third-party risk management, cybersecurity and other risk management use cases — ultimately establishing a strong defense against the ever-changing threats to your business.
Featured Risk Management Solutions
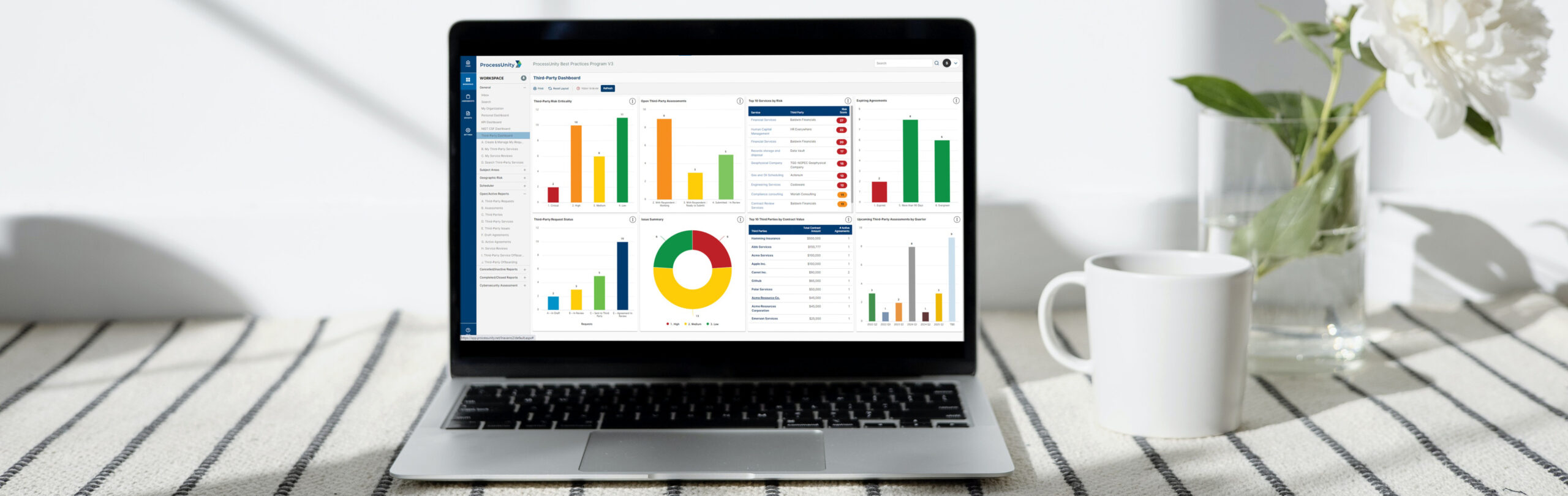
-
Third-Party Risk Management
Protect your organization against third-party, vendor and supplier risk
Learn More: Third-Party Risk Management -
Cybersecurity Risk Management
Gain enterprise-wide visibility into cybersecurity preparedness
Learn More: Cybersecurity Risk Management -
The ProcessUnity Platform
Powerful, no-code platform solves organizations' top risk management challenges
Learn More: The ProcessUnity Platform
Powerful, Configurable Platform Provides Best-in-Class Risk Solutions
The ProcessUnity Platform delivers customer-driven, purpose-built solutions that work together to unify risk management processes throughout the enterprise. Active customer use cases include:
- Advertising Compliance
- Anti-Bribery and Corruption (ABAC)
- AWA Compliance
- Case Management
- Broker-Dealer Compliance
- Complaint Management
- Consortium Marketplace
- Contract Risk Management
- Cybersecurity Risk Management
- Document Management
- Exam and Certification Management
- Incident Management
- Internal Ticket Management
- Internal Audit
- IT Application Certifications
- IT Controls Testing
- IT Risk Management
- Managed Service Platform
- Operational Risk Management
- Policy and Procedure Management
- Product Release Management
- Product Utilization Management
- Repo Compliance
- Regulatory Change Management
- Risk Control Self-Assessment (RCSA)
- Service-Level Agreement (SLA) Program
- Statutory Reporting
- Sarbanes-Oxley (SOX) Compliance
- Sourcing / RFx Processes
- Third-Party Risk Management
- Trade Error Management
- Volcker Rule Compliance
Begin your journey to enterprise-wide risk visibility. Contact us below to schedule a live ProcessUnity demonstration.
Request a ProcessUnity Demo
Schedule your personalized demo of our award-winning software and start your journey to a more mature, automated program.
Request a ProcessUnity Demo