Third-Party Risk Management Software
Third-Party Risk Management
ProcessUnity for Third-Party Risk Management (TPRM) protects companies and their brands by reducing risk from third parties, vendors and suppliers. TPRM expands the scope of risk management to encompass any external party that could pose a risk to an organization, including vendors, contractors, partners and suppliers.
Automate the Third-Party Lifecycle
- Pre-Contract
- Post-Contract
- Key Capabilities
Third-Party Onboarding
Automate the vendor onboarding process, establishing a single, standardized, easily accessible and enterprise-wide process for introducing a service provider into your vendor database.
Third-Party OnboardingPre-Contract Due Diligence
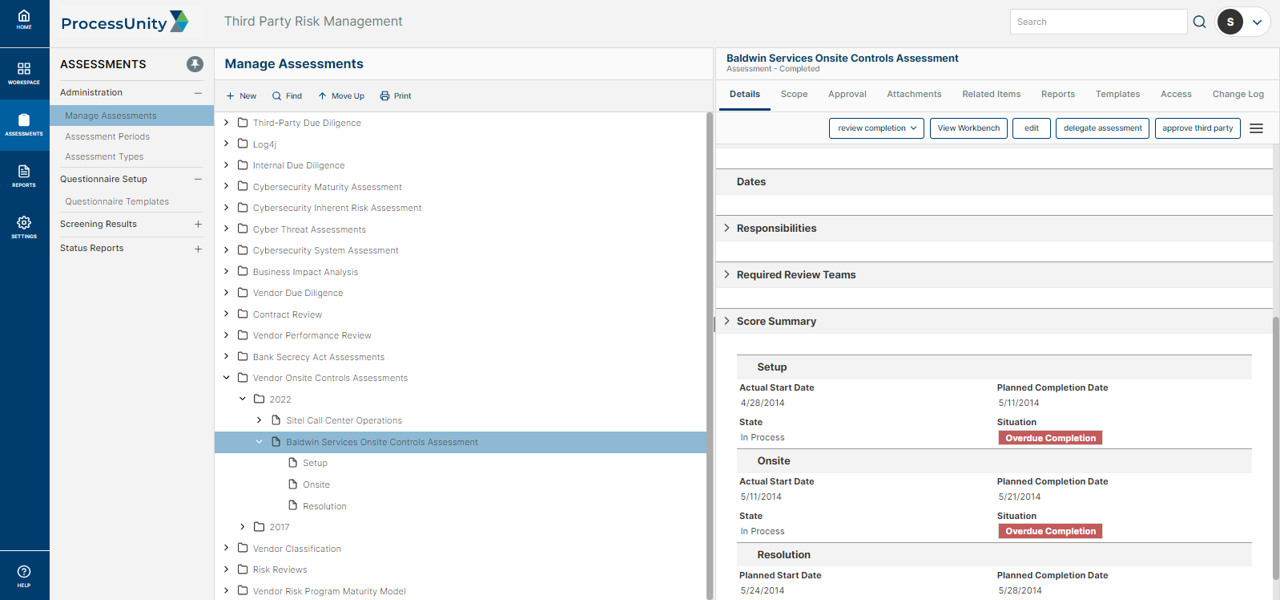
Implement a simplified, automated and efficient third-party risk vendor assessment process for your internal third-party risk analysts and your vendors, suppliers and fourth parties.
Pre-Contract Due DiligenceRisk Domain Screening
Proactively screen vendors against a variety of risk domains, such as financial stability and security, to effectively manage third-party risks and avoid costly disruptions.
Vendor Intelligence SuiteSourcing / RFx Support
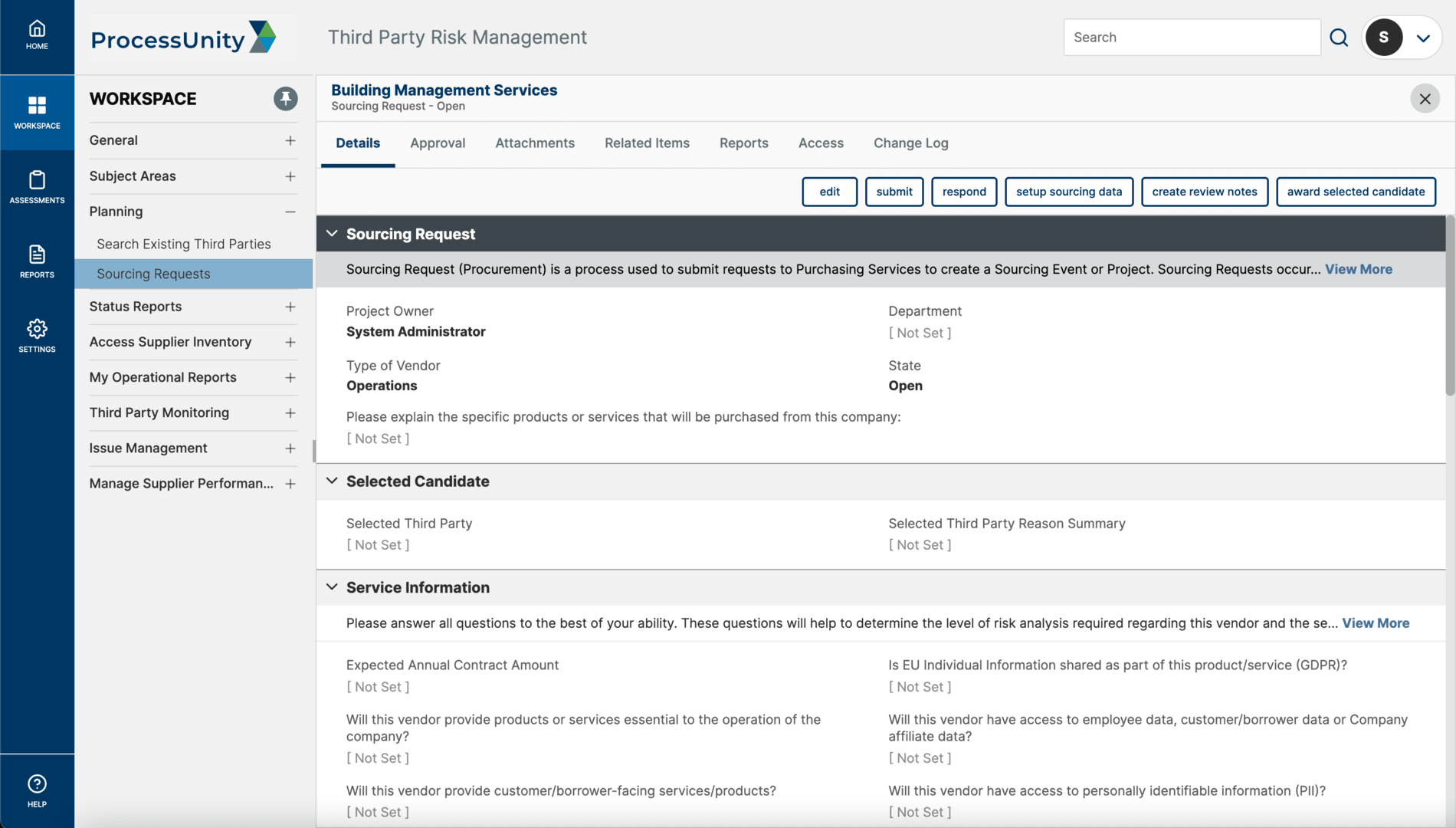
Make the source-to-contract process more efficient by executing RFx processes, performing initial due diligence and driving the awarded vendor through initial onboarding.
Sourcing (RFx)Continuous Third-Party Monitoring
Establish an objective post-contract cadence to proactively monitor vendor activities and detect potential risks in real-time.
Continuous Third-Party MonitoringVendor Performance Management
Maintain a common platform, accessible to all authorized parties, on which they compare vendor performance against established service level agreements (SLAs).
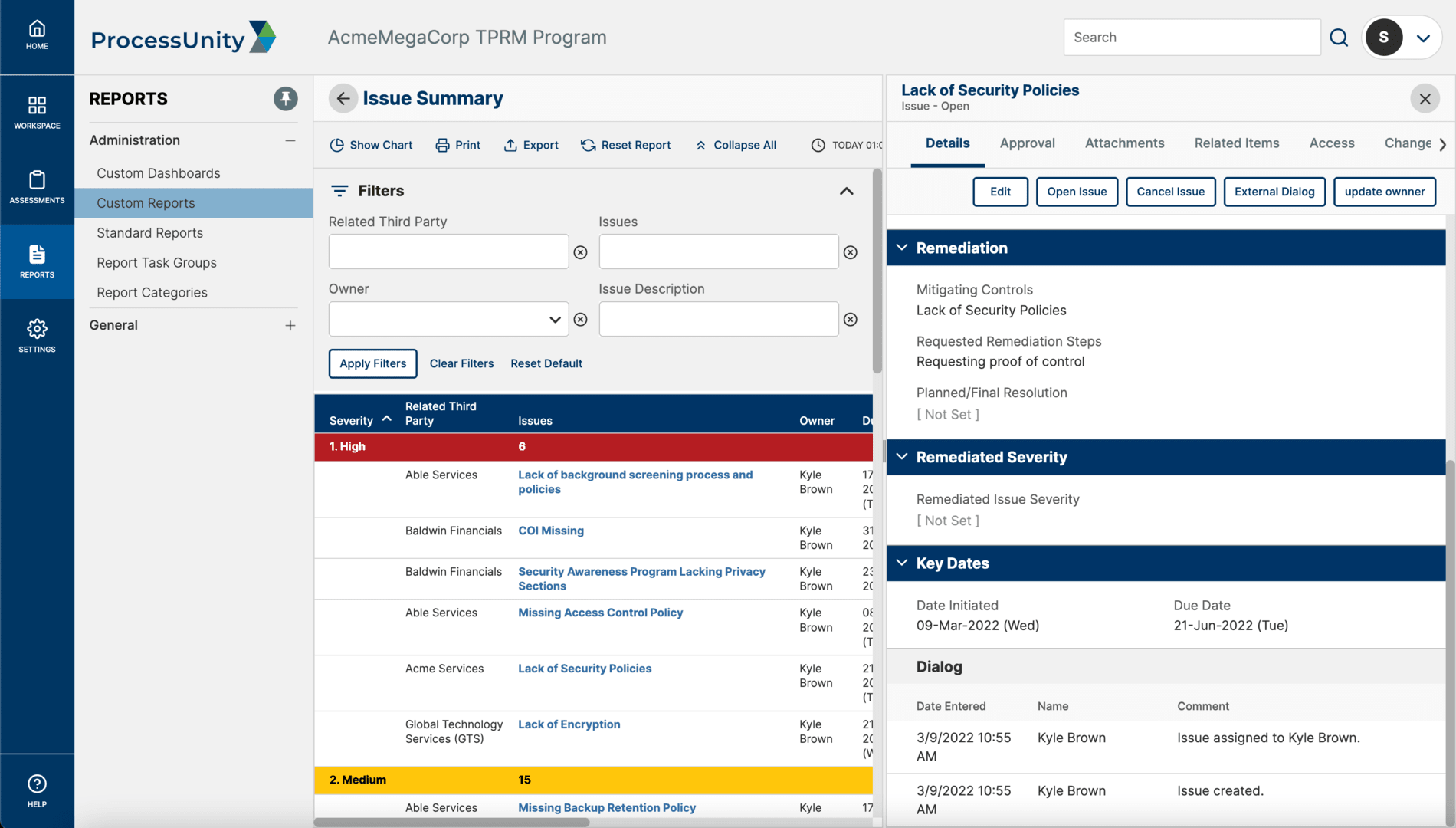
Vendor Performance ManagementIssue Management
Gain step-by-step control to document and record issues, assign responsibilities, track progress on actions and status, and produce reports for appropriate stakeholders.
Issue ManagementPost-Contract Due Diligence
Implement a simplified, automated and efficient third-party risk vendor assessment process for your internal third-party risk analysts and your vendors, suppliers and fourth parties.
Post-Contract Due DiligenceNo-Code Configuration
Easily add features and functionality without relying on service engagements. The ProcessUnity Platform is 100% configurable by the end user, meaning that you don't have to wait weeks for the changes you need to meet program demands.
No-Code ConfigurationHands-Free Automation
Automate everything from assessment scoping to evidence collection with the click of a button. Hands-Free Automation runs critical workflows in the background, so that you can execute on impactful risk reduction.
Hands-Free AutomationEnterprise Integration
Seamlessly integrate with key enterprise systems or external content providers through a robust web services-based API.
Enterprise IntegrationReporting-As-A-Service
Provide stakeholders with the data that matters to them in seconds. Reporting-as-a-Service rapidly generates meaningful, board-ready reports that demonstrate the value of your program.
Reporting-As-A-ServiceThird-Party Risk Management Features & Benefits
Powerful Third-Party Risk Assessment Tools
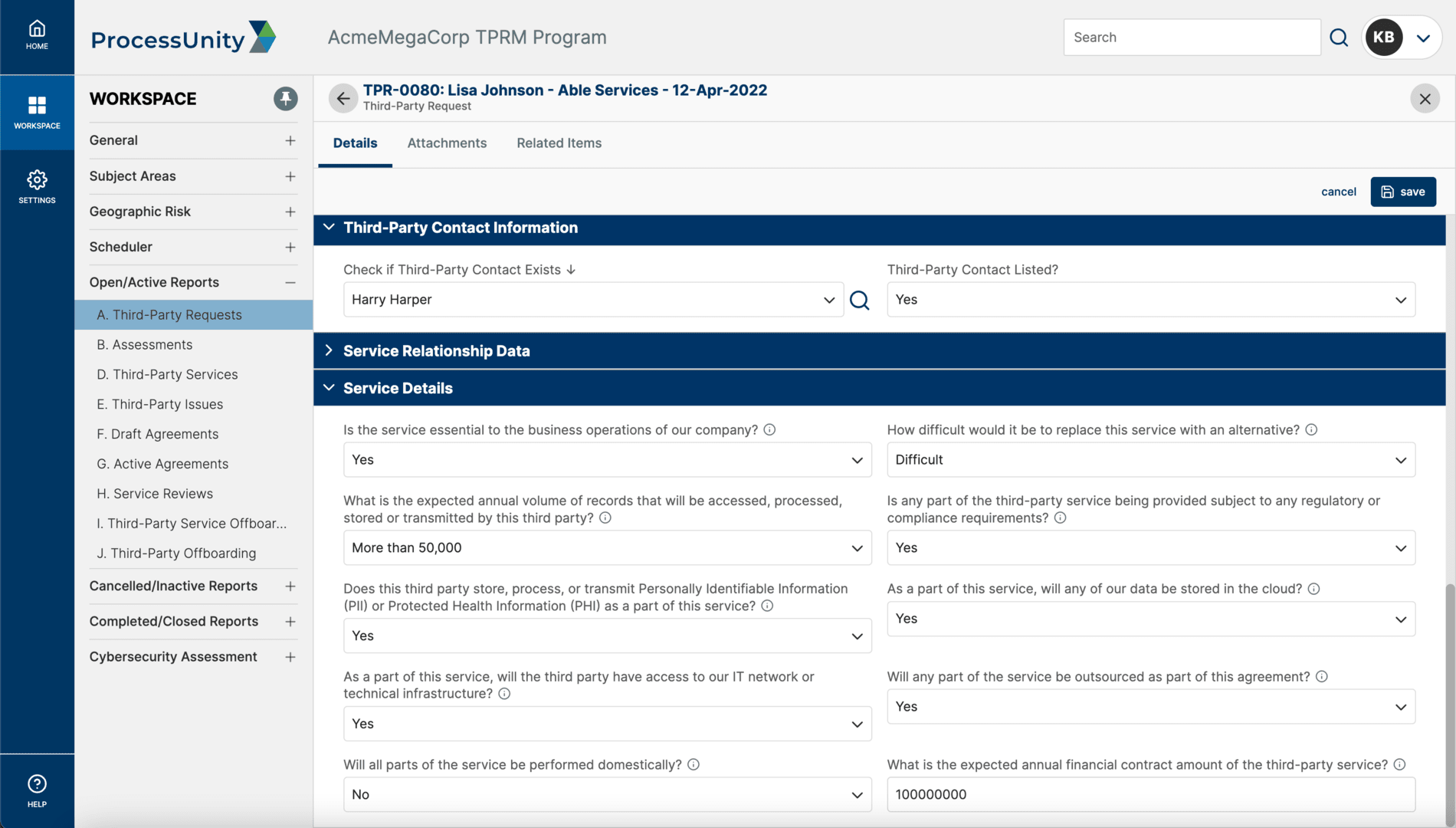
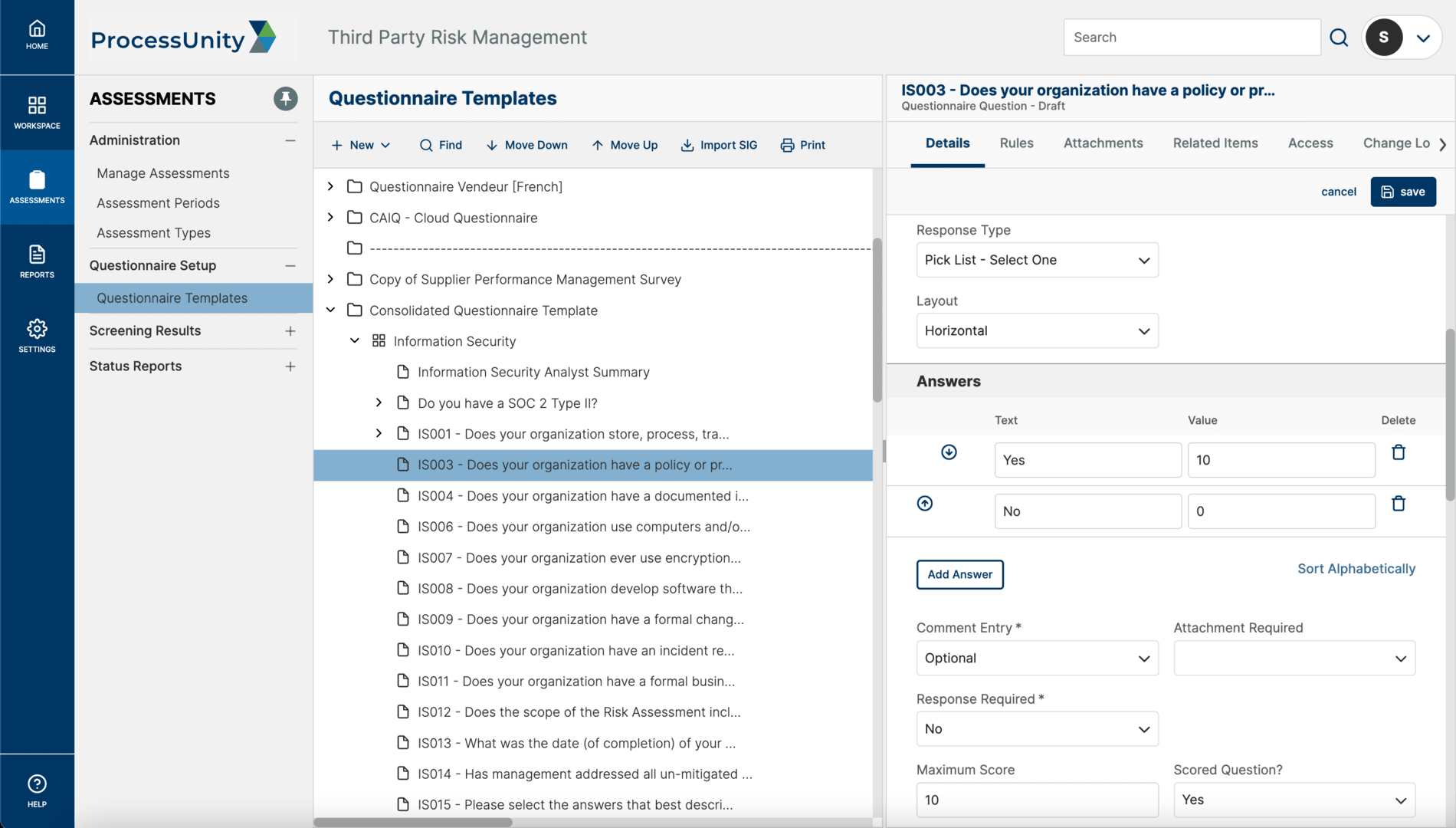
The ProcessUnity intelligent questionnaires transform the third-party risk assessment process by eliminating the inefficiencies of surveys and spreadsheets. Inherent risk scores and vendor criticality tiers automatically determine assessment scope, while preferred responses score vendor submissions in real-time, highlighting areas that require attention. Third-party risk teams can take advantage of built-in content or easily import their own methodologies, including Standard Information Gathering questionnaires (SIG Lite and SIG Core) from Shared Assessments. Third and fourth parties complete assessment questionnaires through a secure online portal, with delegation capabilities to multiple contacts and the ability to attach supporting documentation. With streamlined assessments, organizations can more thoroughly vet more vendors, improving response quality and reducing vendor fatigue.
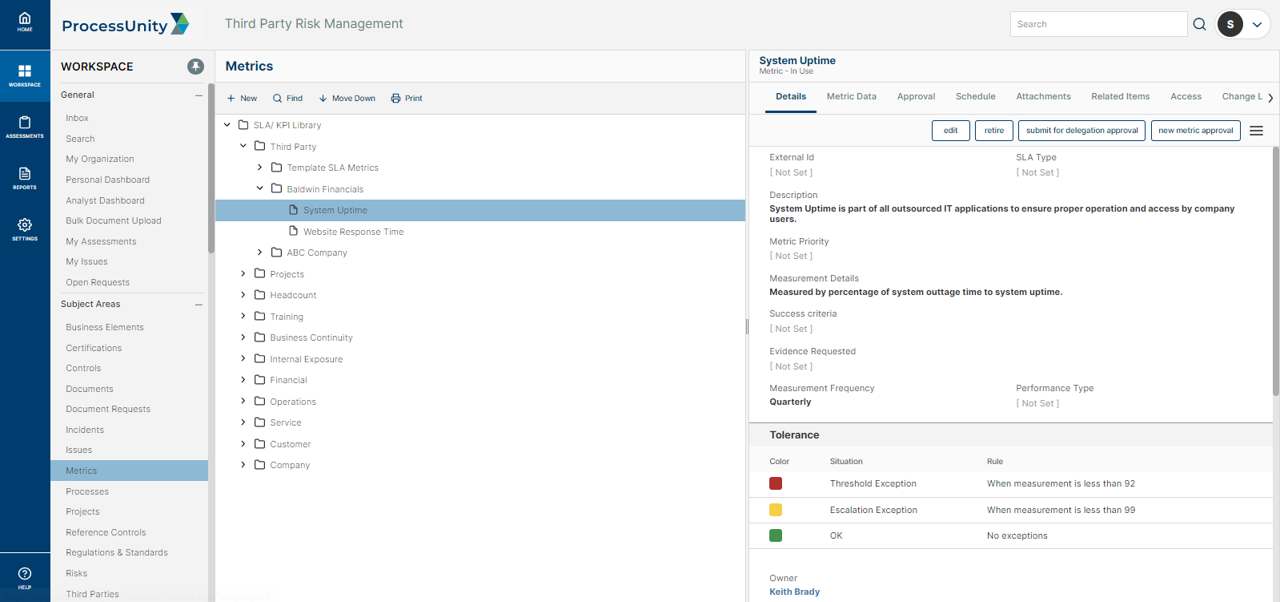
Third-Party Risk Management Reporting & Metrics
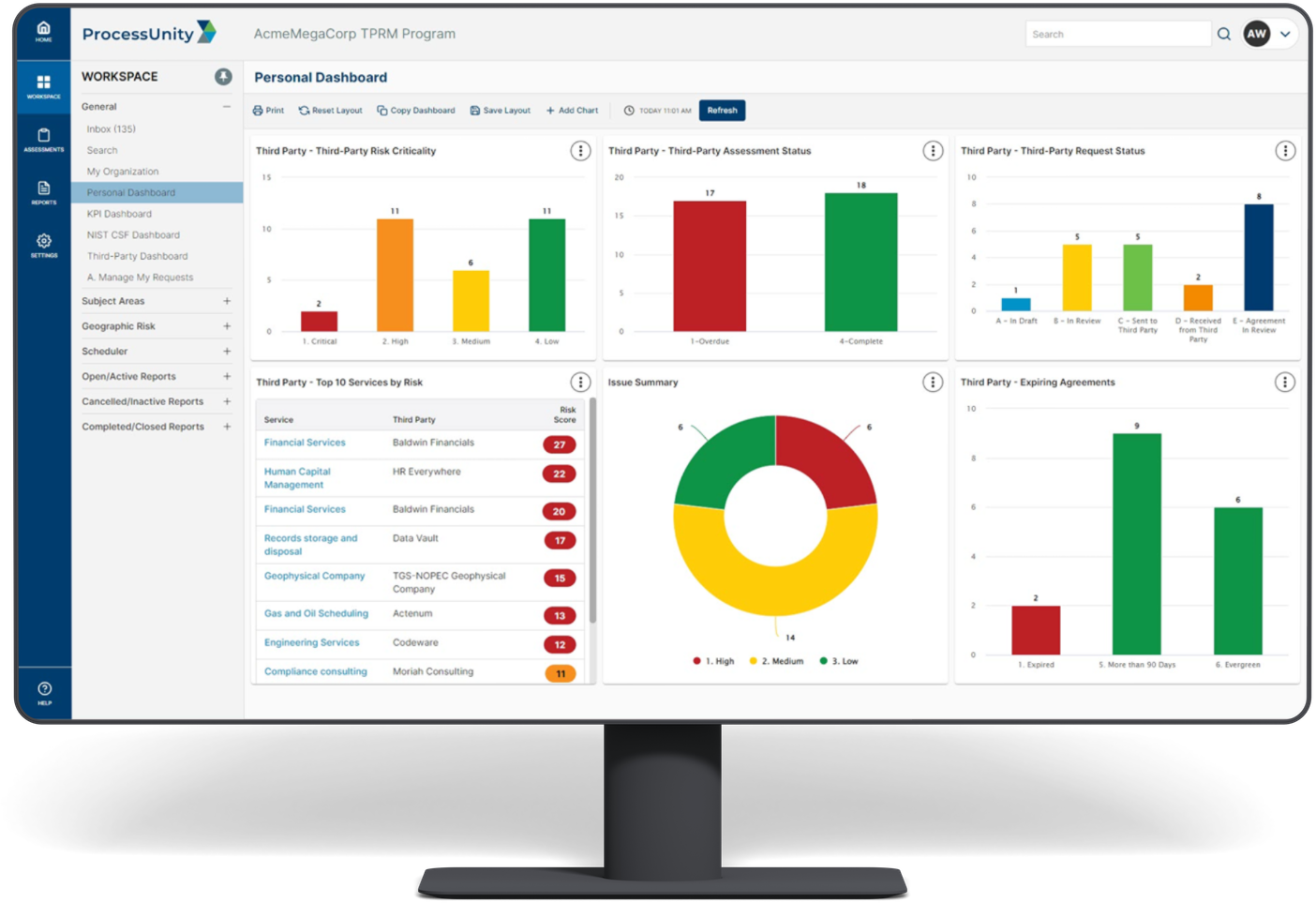
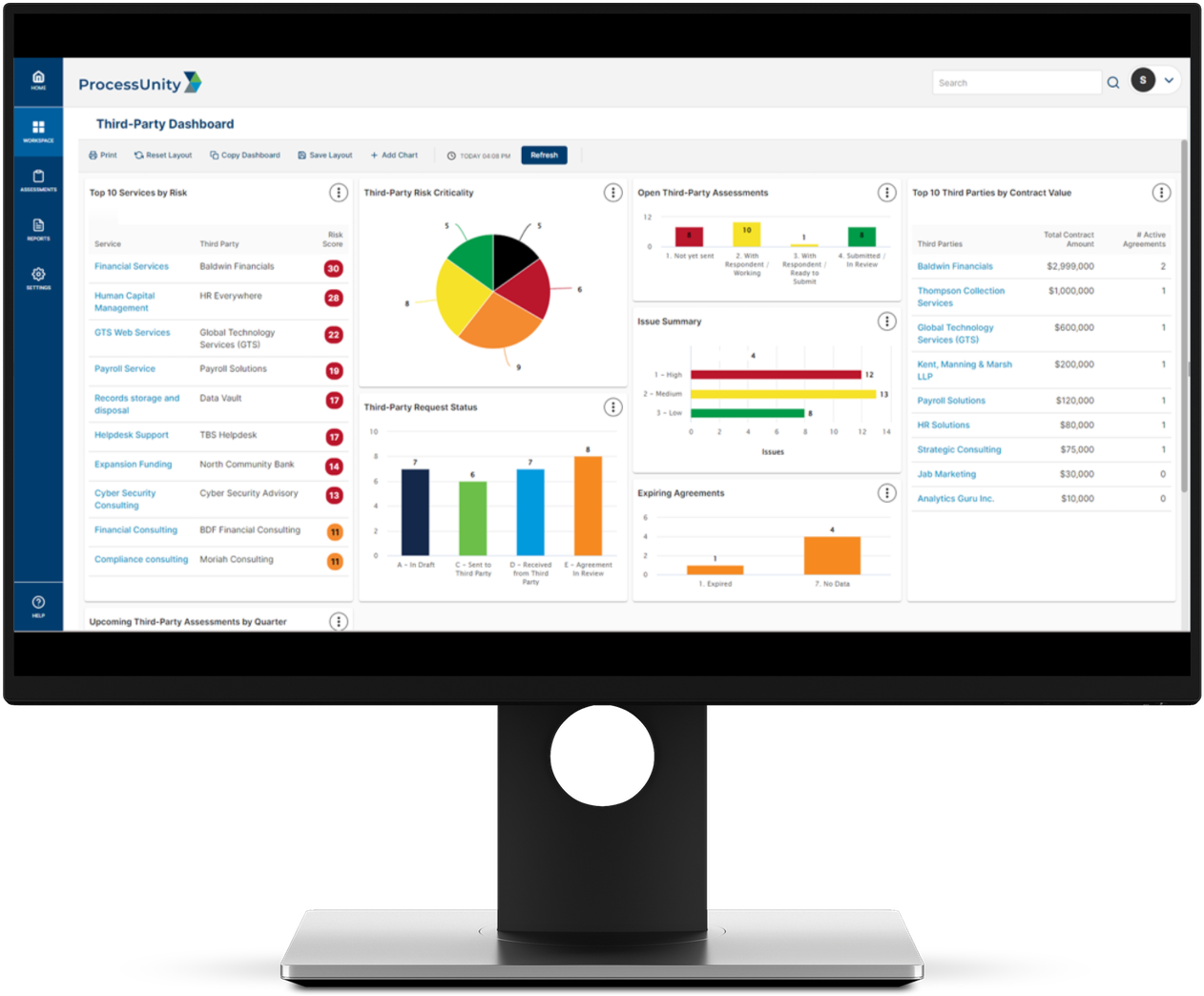
ProcessUnity provides real-time visibility into the state of third-party risk and demonstrates to executives and regulators the existence of a consistent, reliable and repeatable program. Interactive dashboards give management visibility into ongoing risk assessment progress, the status of remediation activity and vendor ratings. Drill-down capabilities allow risk managers to quickly find the details in areas of concern.
Extensive custom reporting capabilities allow risk managers to create role-specific reports and dashboards through the point-and-click interface. With ProcessUnity, organizations gain program-level reporting that manual methods simply cannot provide.
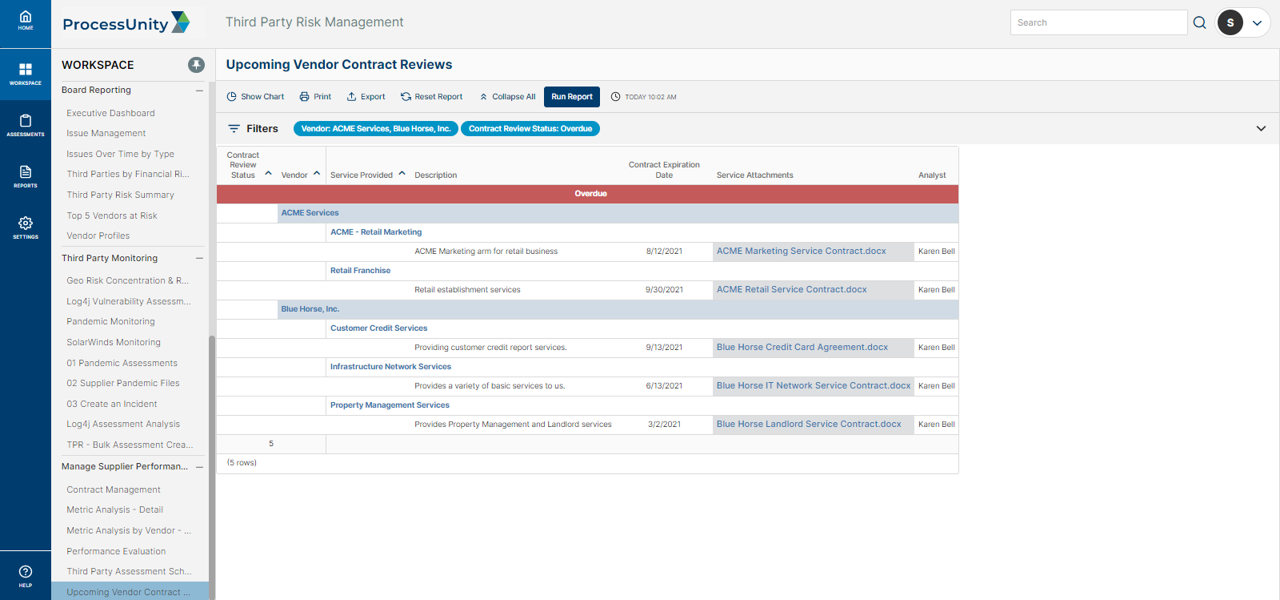
Pre-configured reports track critical vendor and service-risk information, including:
- Vendor Criticality
- Vendor Assessment Status
- Assessment Findings
- Issues
- Requests
- Action Items
- Contract Review Status
- Risk by Geographic Location
- Compliance Ratings
Integration with Cybersecurity Ratings, Financial Health Scores & External Expert Content
Third-party risk teams can incorporate industry-vetted content to augment initial vendor assessments and to signal potential issues in between periodic due diligence. With a variety of pre-built connectors to cybersecurity ratings, financial health metrics, watch lists, negative news feeds and more, ProcessUnity provides customers with additional insights into vendor preparedness, stability and performance.
Learn more about the ProcessUnity pre-built connectors that can enhance and augment Third-Party Risk Management programs.
Flexible Deployment Options + Unparalleled Configuration = Future-Proof Deployments
ProcessUnity for Third-Party Risk Management supports organizations of all sizes and program maturity. Our pre-built, out-of-the-box Best Practices Configuration offers smaller vendor risk teams a quick-to-deploy, complete program based on hundreds of successful customer deployments. Organizations with the most demanding and complex requirements can take advantage of the unparalleled configurability of the ProcessUnity Platform to implement a program that 100% matches their specifications.
No matter how ProcessUnity is deployed, customers always have the flexibility to make changes to their implementation as their programs change and mature over time, future-proofing their Third-Party Risk Management software investment.
Request a Demo: Third-Party Risk Management
Hundreds of organizations worldwide rely on ProcessUnity to make Third-Party Risk Management more effective and efficient. Schedule your personalized demo of our award-winning software and start your journey to a more mature, automated vendor risk management program today!
Request a Demo: Third-Party Risk Management