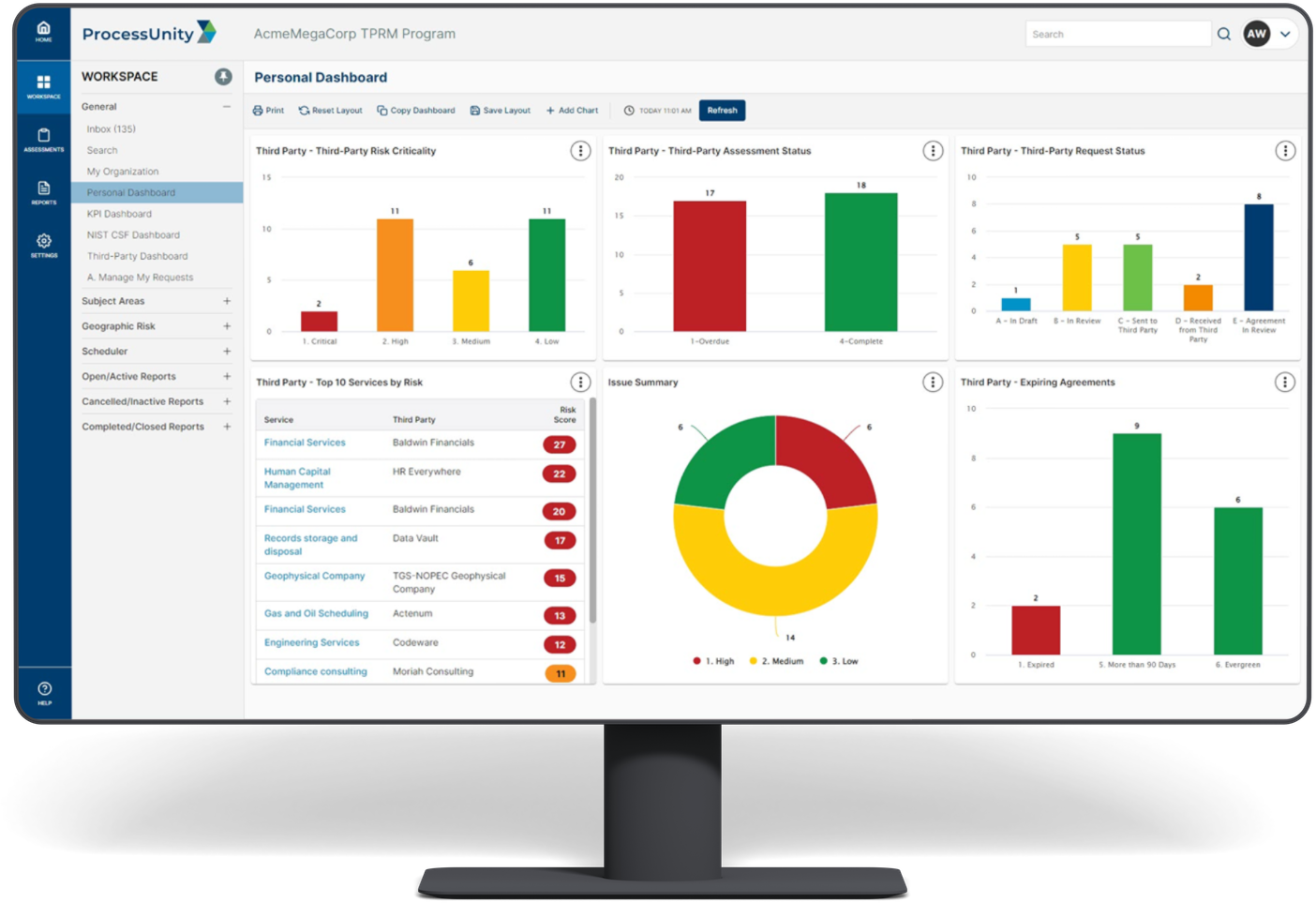
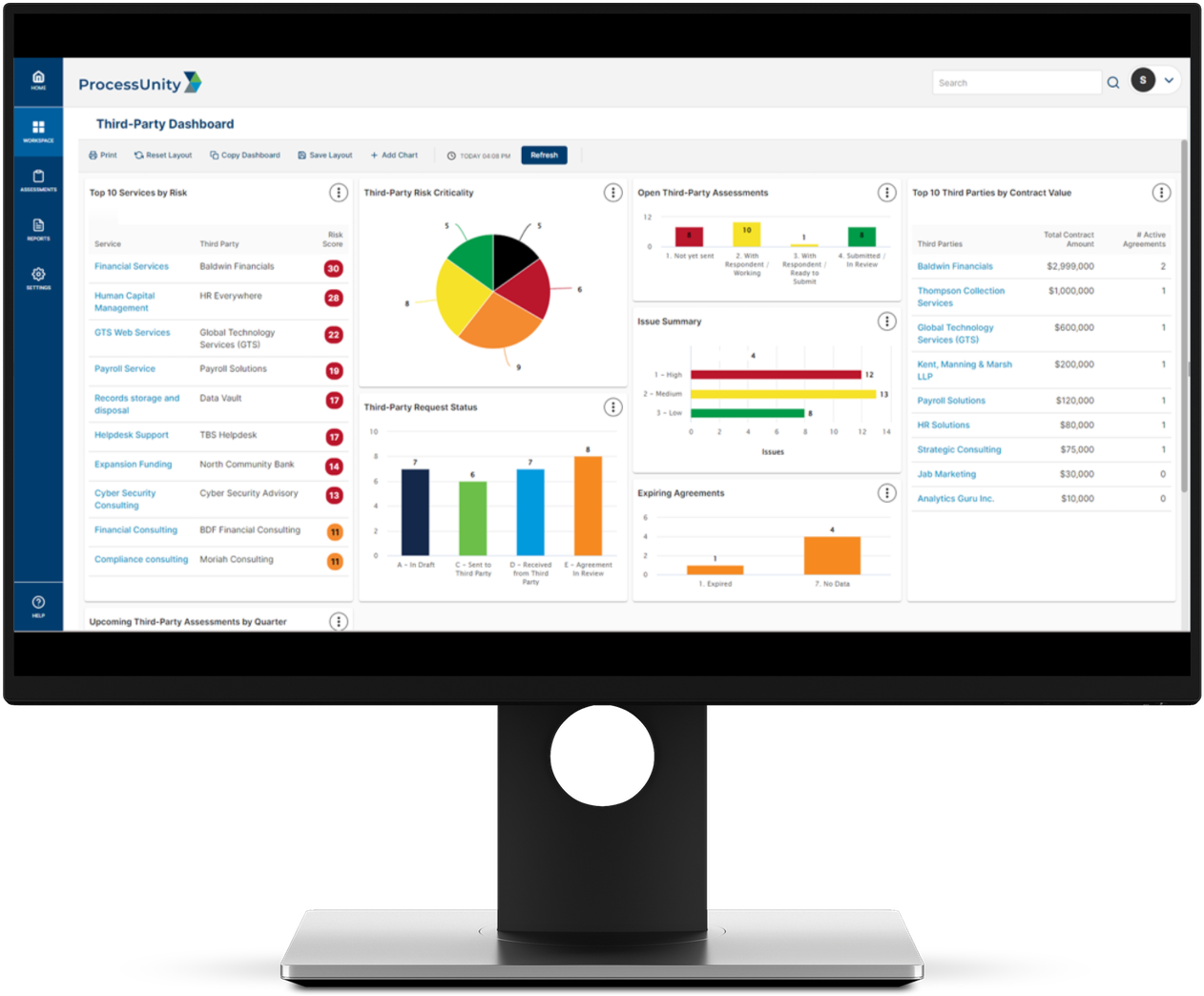
Third-Party Risk Management Software
Third-Party Risk Management Platform
At the heart of an effective Third-Party Risk Management (TPRM) strategy, lies the ProcessUnity TPRM Platform. As one of the four pillars of our end-to-end TPRM solution, the ProcessUnity TPRM platform works in sync with our Universal Data Core, Global Risk Exchange and AI-Powered teams to deliver a comprehensive and proactive approach to managing third-party risk.

With a single, configurable platform, ProcessUnity helps organizations manage the increasing complexity of supply chains and third-party relationships with tools to identify and assess the risks associated with each external party, monitor third-party performance and ensure external control effectiveness. Our software empowers you to proactively manage third-party risks and protect your organization from potential cyber threats and business disruptions.
Benefits Summary
- Onboard Vendors Faster: ProcessUnity simplifies the onboarding process via a configurable, automated process, reducing cycle times and ensuring consistency in the evaluation of potential third-party risks.
- Streamline Post-Contract Vendor Assessments & Monitoring: The ProcessUnity TPRM platform reduces assessment backlog and keeps tabs on critical third parties in between period assessments. Integrated ratings and scores from external data providers allow you to confirm assessment responses and send alerts when things change.
- Extend Vendor Oversight: ProcessUnity allows for meticulous oversight of your entire third-party ecosystem, reducing risk and ensuring compliance with key regulations, standards and frameworks.
- Generate Reports & Insights in Real-Time: With ProcessUnity, you have access to real-time reporting and highly configurable dashboards. With a single click, your team gains an immediate understanding of your third-party risk posture for timely decision-making and risk mitigation.
Measurable Efficiency Gains, Proven Customer Value
Independent research from GRC 20/20 found that ProcessUnity delivered significant customer benefits across the Third-Party Risk Management lifecycle, including:
- 50% reduction in third-party risk oversight and management
- 85% reduction in third party onboarding time
- 85% reduction in post-contract risk assessments
- 90% reduction in third-party risk reporting, metrics and analytics
Learn more: Download GRC 20/20’s Value Perspective on ProcessUnity.
Supported TPRM Processes & Workflows
Click the links below to learn how the ProcessUnity TPRM Platform brings new levels of efficiencies to key Third-Party Risk Management processes:
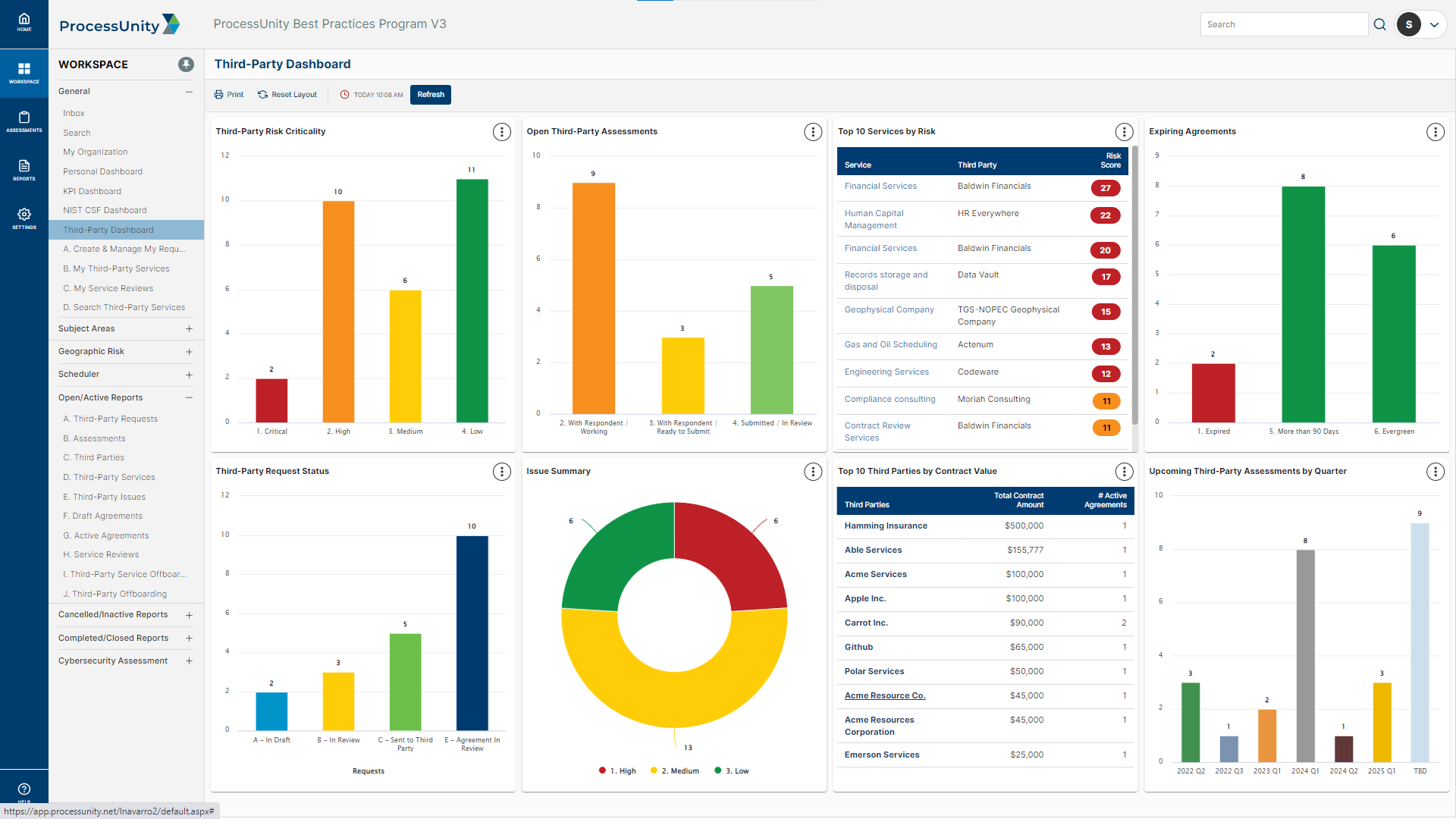
- Platform Differentiators
No-Code Configuration:
With ProcessUnity, there's no need for complicated coding knowledge. Our platform offers intuitive tools for easy configuration, allowing you to build and modify screens, alerts, notifications and workflows to suit your program requirements.
No-Code ConfigurationHands-Free Automation:
ProcessUnity leverages advanced automation capabilities, providing seamless and efficient task management. It automates recurring processes, reducing manual intervention, ensuring consistency and minimizing errors.
Hands-Free AutomationEnterprise Integration:
ProcessUnity ensures smooth integration with your existing enterprise systems, enabling data sharing and synchronization across platforms. This enhances visibility, improves decision-making and streamlines third-party risk management.
Enterprise IntegrationReporting-as-a-Service:
The ProcessUnity TPRM platform delivers real-time, sophisticated reporting capabilities. With our reporting-as-a-service feature, you can generate insightful reports and dashboards at the click of a button, providing a clear view of your third-party risk landscape.
Reporting-As-A-ServiceFlexible Deployment Options
Regardless of a company’s stage of growth and maturity, the ProcessUnity TPRM Platform offers scalable solutions tailored to specific needs. Organizations in the early stages of developing their risk management protocols can take advantage of our out-of-the-box program components and best practices to speed development. For more established corporations with complex processes, ProcessUnity provides powerful tools and unparalleled configurability to solve the toughest challenges. Our platform’s inherent flexibility and adaptability allow for seamless integration into various third-party risk management workflows. ProcessUnity grows with your company, ensuring continued support and risk mitigation as your requirements evolve and third-party networks expand.
End-to-End Third-Party Risk Management
The ProcessUnity TPRM Platform is a critical component of ProcessUnity’s comprehensive approach to Third-Party Risk Management. When combined with the Universal Data Core, our Global Risk Exchange and AI-powered teams, it creates a potent, end-to-end solution that transforms the way businesses handle third-party risk.
Get Started with ProcessUnity
Ready to revolutionize your Third-Party Risk Management strategy? With the ProcessUnity TPRM Platform, gain unprecedented insights, reduce assessment work, and proactively mitigate risks like never before. Join the ranks of industry-leading firms who rely on ProcessUnity for their TPRM needs. Don’t wait, take control of your risk landscape today. Get started with ProcessUnity.
Request a Demo: Third-Party Risk Management
Hundreds of organizations worldwide rely on ProcessUnity to make Third-Party Risk Management more effective and efficient. Schedule your personalized demo of our award-winning software and start your journey to a more mature, automated vendor risk management program today!
Request a Demo: Third-Party Risk Management