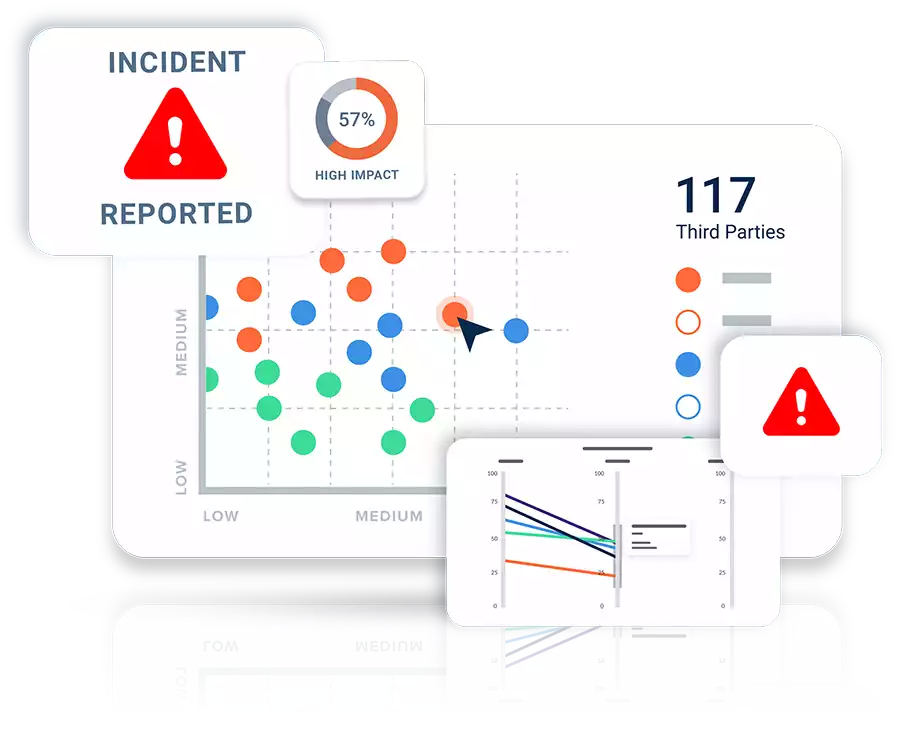
Third-Party Cyber Risk Management Software
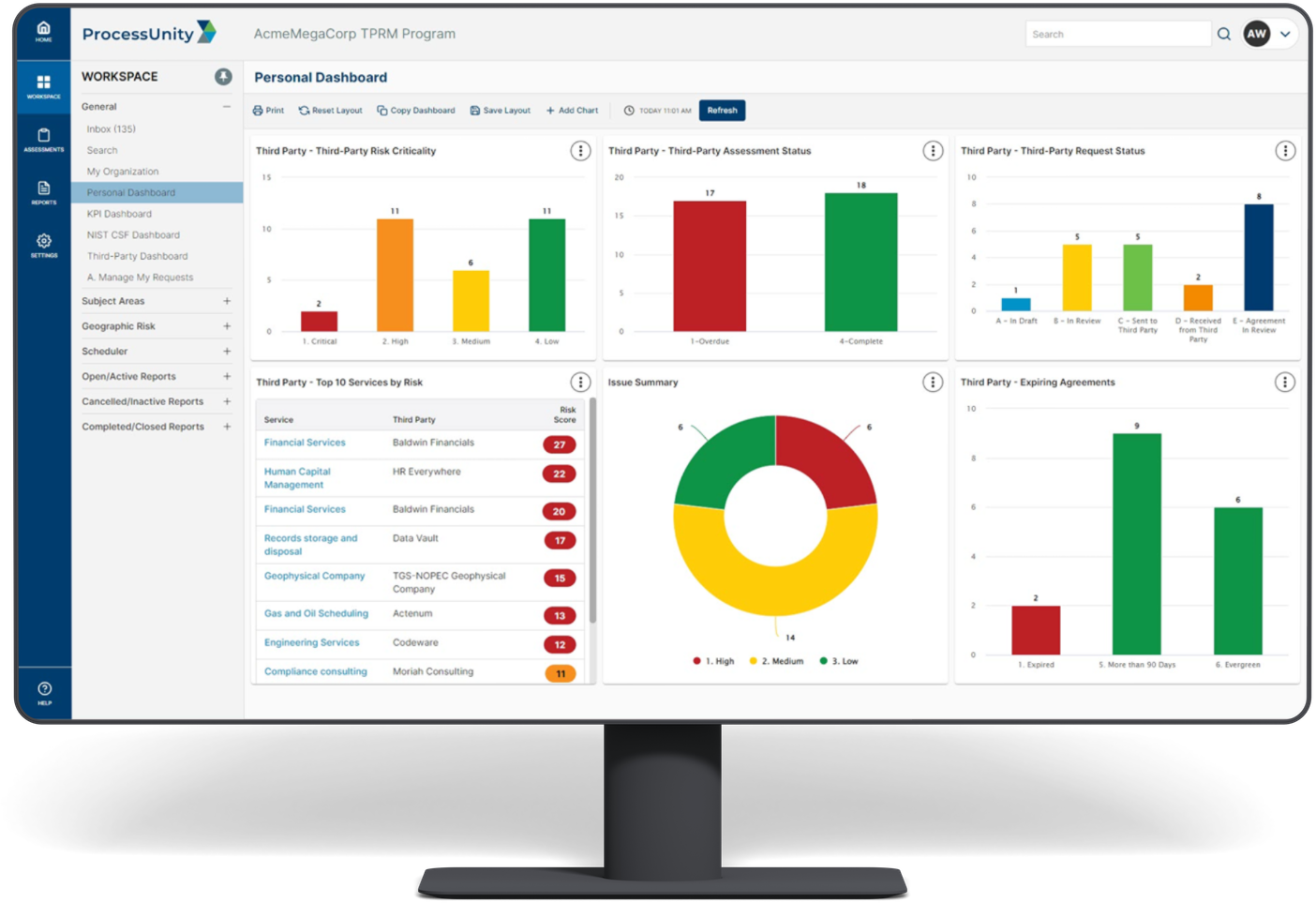
Third-Party Threat Tools
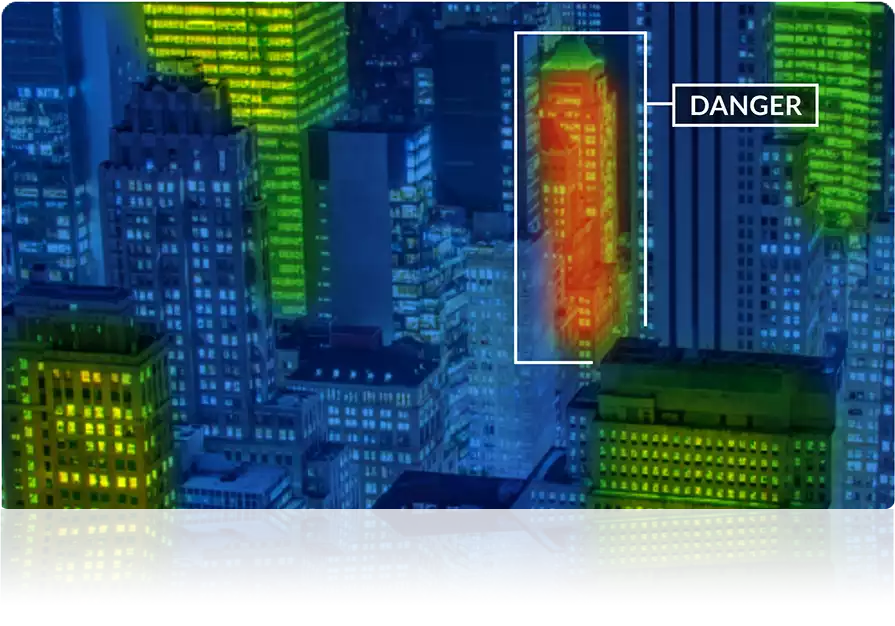
Proactively identify, analyze, and monitor potential security threats.
Our suite of threat tools enables you to understand vulnerabilities across your third-party ecosystem, so you can take action to reduce your risks and minimize the impact of an attack.
Three Steps to Get Started:
- Upload your list of third parties into our Exchange.
- Discover your blindspots.
- Manage your third-party cyber risk confidently.
Request a Demo: Third-Party Risk Management
Hundreds of organizations worldwide rely on ProcessUnity to make Third-Party Risk Management more effective and efficient. Schedule your personalized demo of our award-winning software and start your journey to a more mature, automated vendor risk management program today!
Request a Demo: Third-Party Risk Management